| George Baryannis | Manuel Carro | Dimitris Plexousakis |
| Department of Computer Science | School of Computer Science | Department of Computer Science |
| University of Crete | Universidad Politécnica de Madrid (UPM) and | University of Crete |
| GR 71409 Heraklion, Greece | IMDEA Software Institute, Madrid, Spain | GR 71409 Heraklion, Greece |
| Email: gmparg@csd.uoc.gr | Email: manuel.carro@imdea.org | Email: dp@csd.uoc.gr |
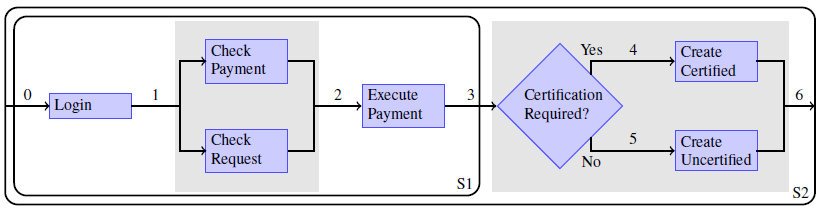
| Service | Preconditions | Postconditions |
| Login | Valid(user,si) ∧¬LoggedIn(user,si) | LoggedIn(user,so) |
| CheckRequest | FilledIn(request,si) ∧LoggedIn(user,si) | Valid(request,so) |
| CheckPayment | FilledIn(payForm,si) ∧LoggedIn(user,si) | Valid(payForm,so) |
| ExecutePayment | Valid(payForm,si) | PayCompleted(doc, user,so) |
| CreateCertified | PayCompleted(doc, user,si) | CertifCompleted(doc, user,so) ∧ Delivered(certifDoc,so) |
| CreateUncertified | PayCompleted(doc, user,si) | Delivered(doc,so) |
|
|
|
|
|
| (4) |
|
| |||||||
| (7) |
| ||||||||
| |||||||||||||||||||||||
| |||||||||||||||||||||||
|
| |||||||
|
| |||||||||||||||
|
| |||||||||||||||
| |||||||||||||||
| (18) |
| |||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||
| Construct | Precondition | Postcondition |
| Sequence | PA(x, a) ∧QA(x, z, b) ∧PB(z, b) | QA(x, z, b) ∧QB(z, y, c) |
| AND-Split/Join | PA(x, a) ∧PB(w, b) | QA(x, z, c) ∧QB(w, y, d) |
| OR-Split/Join | PA(x, a) ∧PB(w, b) | QA(x, z, c) ∨QB(w, y, d) |
| XOR-Split/Join | PA(x, a) ∧PB(w, b) | QA(x, z, c) ⊕QB(w, y, d) |
| Conditional | (C(u, e) ∧PA(x, a)) ∨(¬C(u, e) ∧PB(x, b)) | (C(u, e) ∧QA(x, y, c)) ∨ (¬C(u, e) ∧QB(x, y, d)) |
|
|
| |||||||||||||||